[wolvctf] writeup(s)
https://ctftime.org/event/2240
I participated wolvctf as the KUICS team and scored 15th among 622 teams.
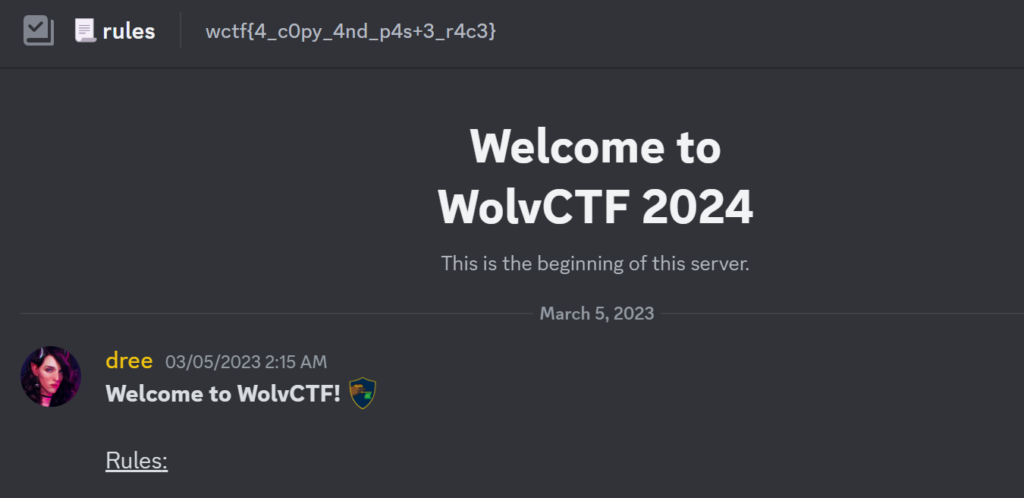
Sanity Check
wctf{4_c0py_4nd_p4s+3_r4c3}
[rev] doubledelete’s revenge
wctf{i_th1nk_y0u_m1sund3rst00d_h0w_r0t13_w0rk5}
Value: 100
Solve Count: 105
Description:
The notorious WOLPHV group has re-emerged and doubledelete is now ransoming us for our flags! Can you help us so we don’t have to pay them?
https://github.com/WolvSec/WolvCTF-2024-Challenges-Public/tree/master/rev/doubledeletes_revenge
The problem gives flag.txt.enc. To get the flag reverse engineering of the encryption algorithm is needed for the given binary.
#include <stdio.h> #include <stdint.h> // For uint32_t, uint64_t #include <Windows.h> static uint32_t __ROR4__(uint32_t x, unsigned int count) { count %= 32; return (x << (32 - count)) | (x >> count); } int __fastcall main(int argc, const char** argv, const char** envp) { int i; // [rsp+14h] [rbp-5Ch] FILE* stream; // [rsp+18h] [rbp-58h] FILE* s; // [rsp+20h] [rbp-50h] DWORD ptr[14]; // [rsp+30h] [rbp-40h] BYREF if (argc == 3) { stream = fopen(argv[1], "r"); fread(ptr, 1uLL, 0x30uLL, stream); for (i = 0; i <= 11; ++i) ptr[i] = __ROR4__(ptr[i], 13); s = fopen(argv[2], "wb"); fwrite(ptr, 1uLL, 0x30uLL, s); return 0; } else { return 1; } }
[rev] Game Graphics Debugging
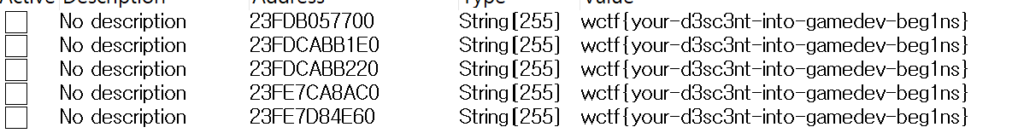
wctf{your-d3sc3nt-into-gamedev-beg1ns}
Value: 428
Solve Count: 33
Description:
I put a flag in this game, but I can’t see it! Can you find it for me?
https://github.com/WolvSec/WolvCTF-2024-Challenges-Public/tree/master/rev/graphics
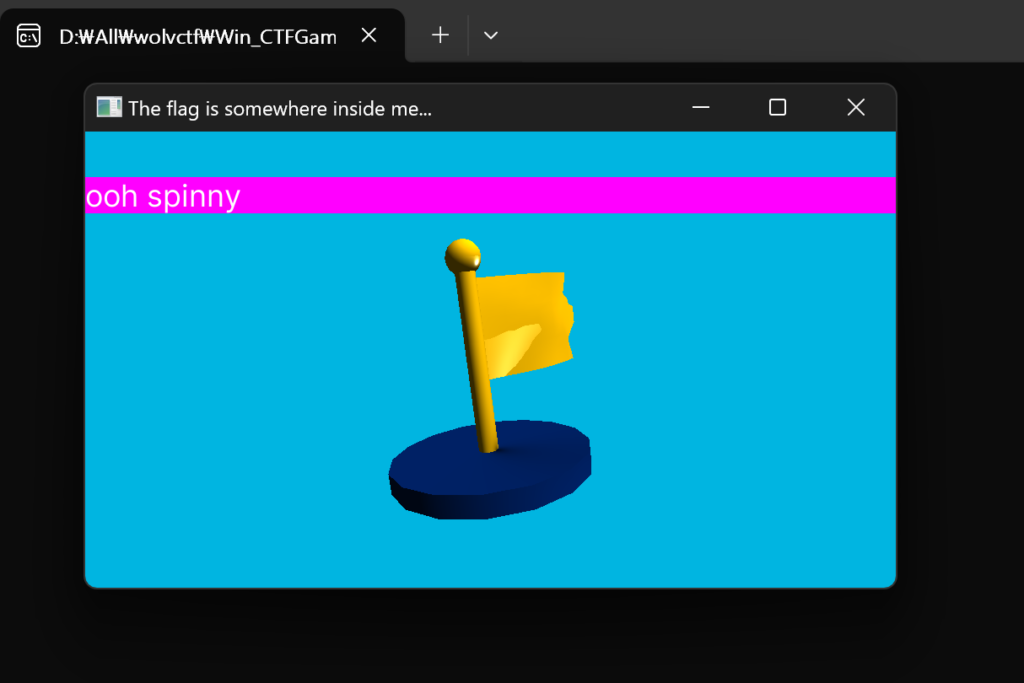
It says that the flag is somewhere inside the game. I used cheat engine to find the flag that were remaining somewhere in memory.
[rev] Missing Resources
Value: 323
Solve Count: 51
Description
My flag is somewhere in this game, but I lost the source code and most of the resources! Can you retrieve it for me?
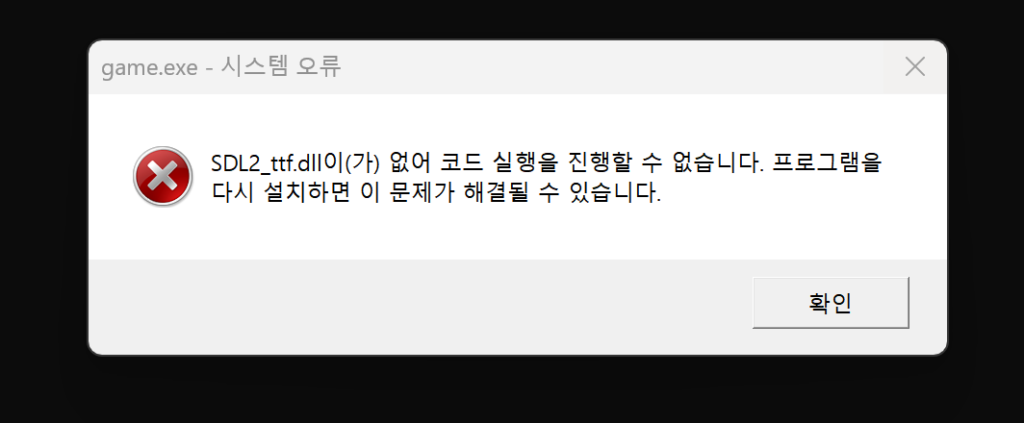
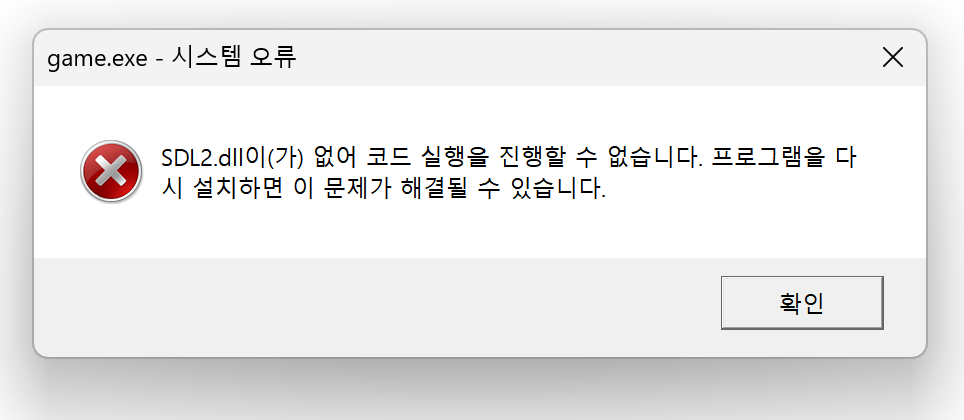
The given binary does not runs, saying that above resources are missing.
I found above resources from the internet and pasted to the folder. However, after running the program will instantly close.
Though, from running from the command line, it can identify why it is closing.
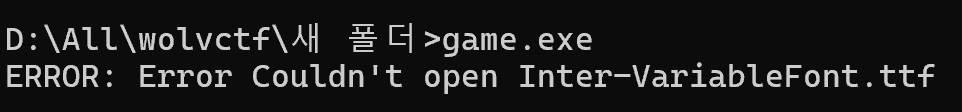
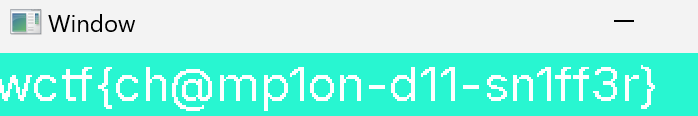
It says that font is missing, so I pasted some random font in my pc as “Inter-VariableFont.ttf” and runned the program.

[OSINT] WOLPHV I: Reconnaissance
wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}
Value: 100
Solve Count: 213
Description:
A new ransomware group you may have heard about has emerged: WOLPHV
There’s already been reports of their presence in articles and posts.
NOTE: Wolphv’s twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges
This is a start to a 5 part series of challenges. Solving this challenge will unlock WOLPHV II: Infiltrate
I found flag from following twitter:
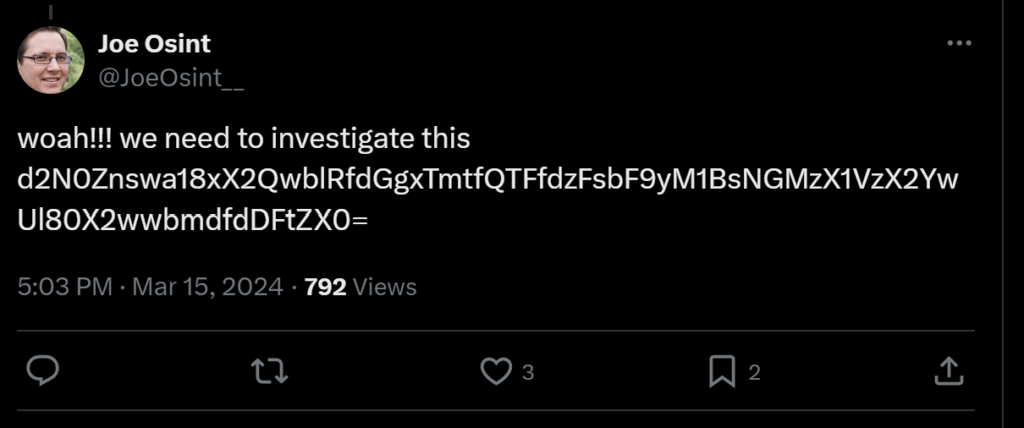
[OSINT] WOLPHV II: Infiltrate
wctf{r0t_52_w0ulD_b3_cr4zy_fRfr}
Value: 100
Solve Count: 93
Unlocked by solving WOLPHV I: Reconissance
Description:
Since the WOLPHV twitter/x is out of commission now, I wonder where else the official WOLPHV group posts on social media. Maybe we can also infiltrate what they use to message each other
NOTE: Wolphv’s twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges
Solving this challege will unlock WOLPHV III, WOLPHV IV, and WOLPHV V

Since google does not give me the scan result of the group, I found it in duckduckgo.
Inside the page there is an interesting video:
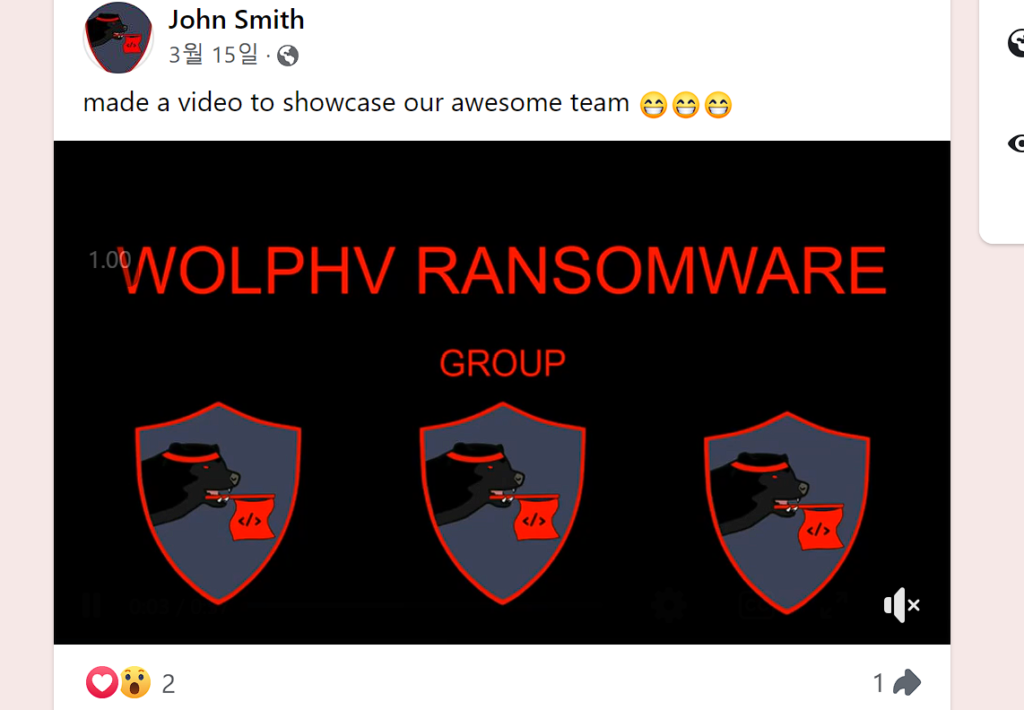
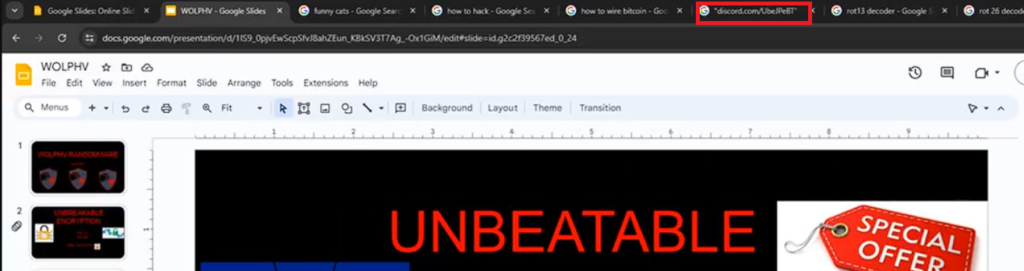
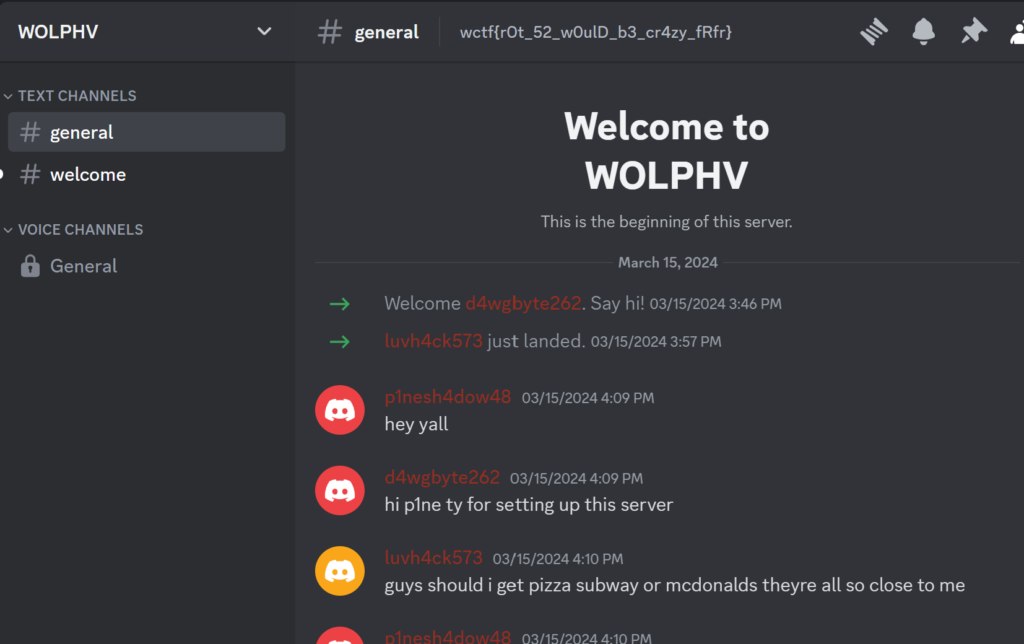
One discord link is being leaked in the video.
Since discord invite link’s domain is .gg, not .com, changing the discord link as .gg will gives the discord server.

Hey people!!!!!
Good mood and good luck to everyone!!!!!