[SEEDLAB] NETWORK SECURITY WRITEUP (Packet Sniffing, ICMP Spoof, Traceroute) #4
What the task wants is to compare the results of packet sniffing runned in normal user and root.
First, I wrote sniff.py which prints icmp packets.
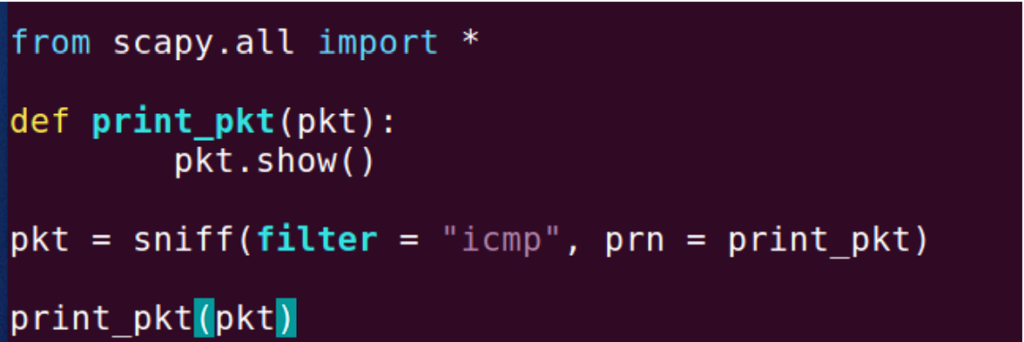
When running in root:
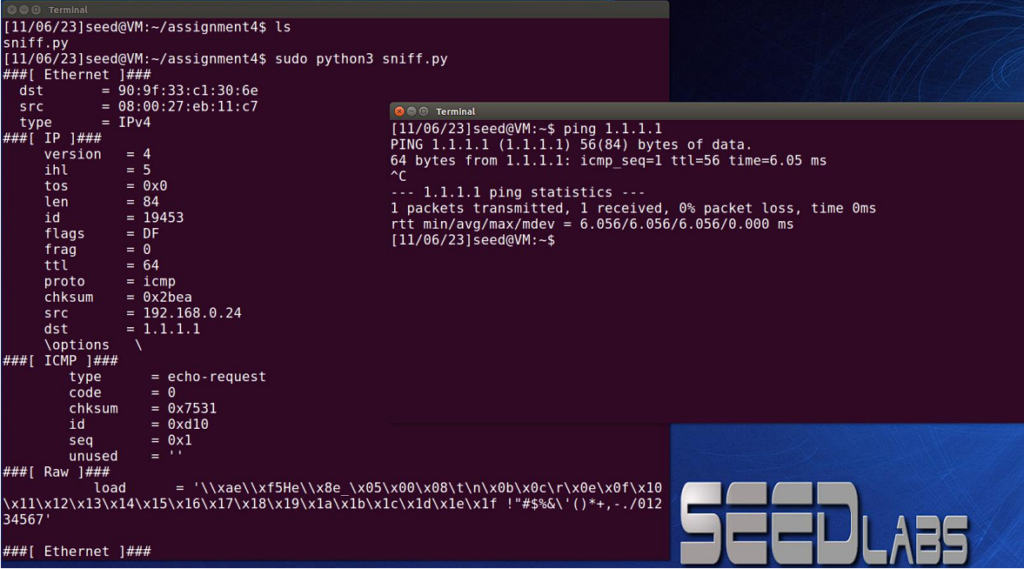
When ping is sent to 1.1.1.1, ICMP packet is successfully captured.
When running in normal user:
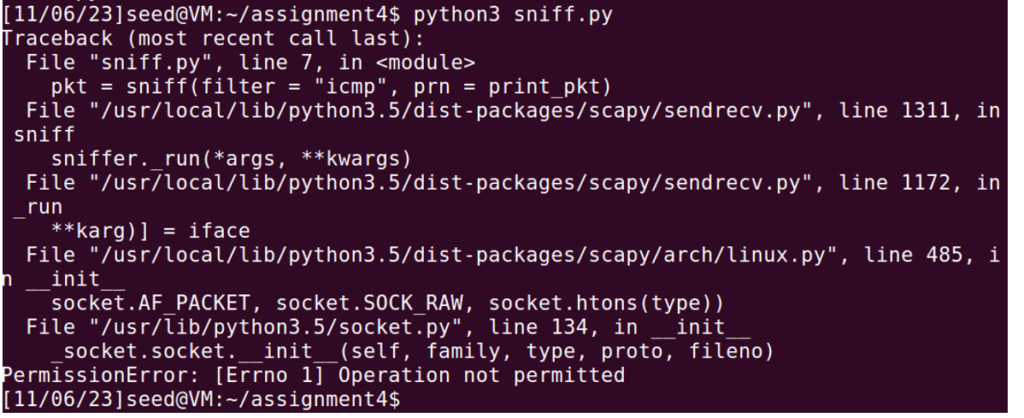
Operation not permitted error is being printed.
Through the task, I can confirm that packet sniffing requires root permission.
Task 1.2 Spoofing ICMP Packet
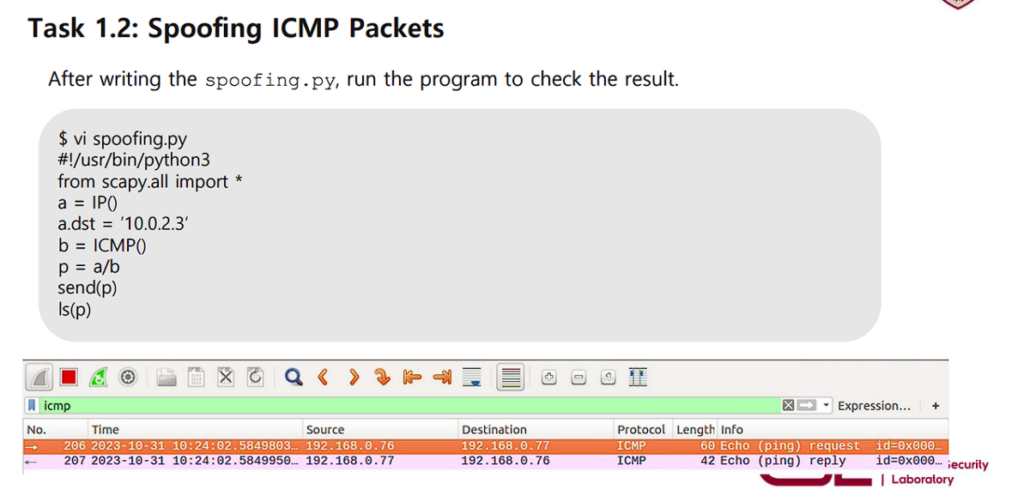
The task requires sending to sent spoofed ICMP packet.
I wrote a code that spoofs Src IP to 123.123.123.123 and sends to 192.168.0.12
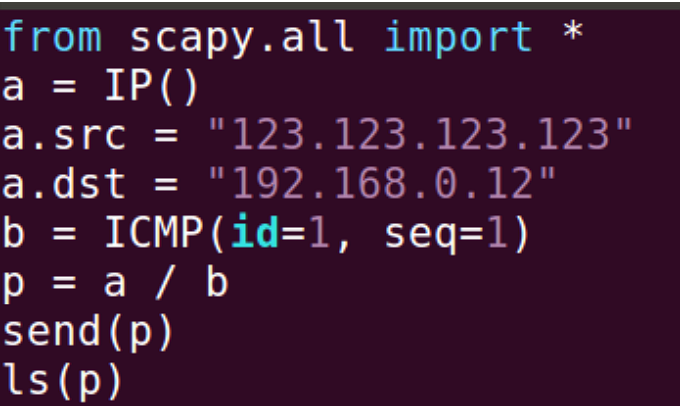
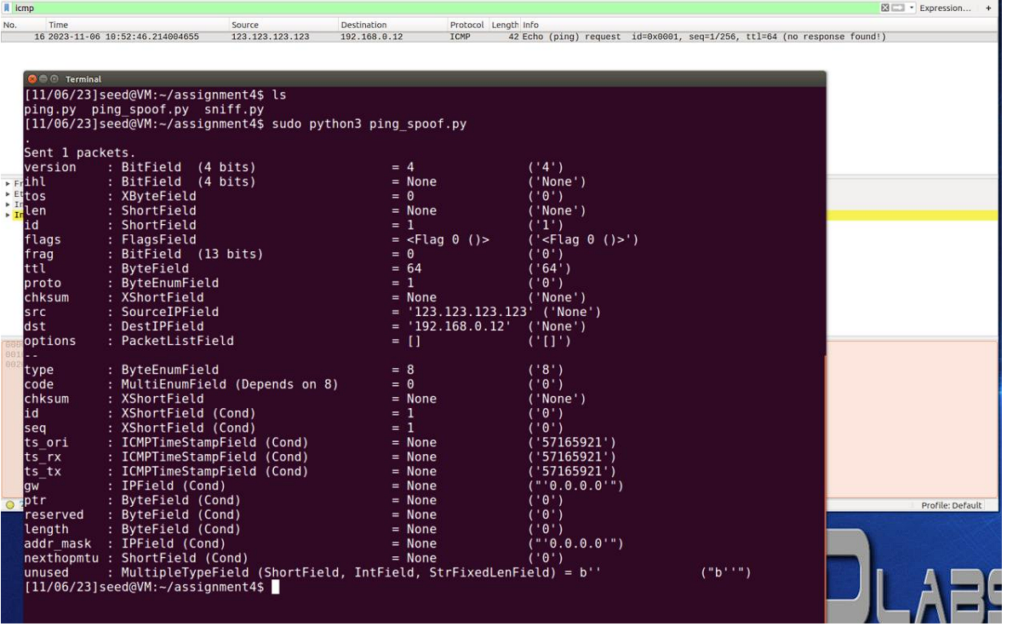
As a result, Src IP successfully spoofed to 123.123.123.123, and it was sent to 192.168.0.12. However, 123.123.123.123 is a non-existent IP address, and therefore I got “no response found!” in Wireshark.
Task 1.3 Traceroute
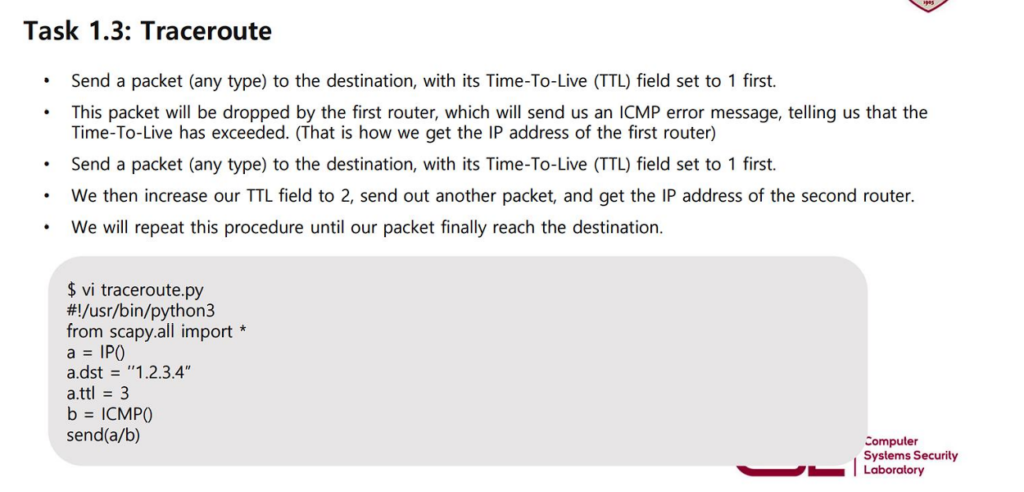
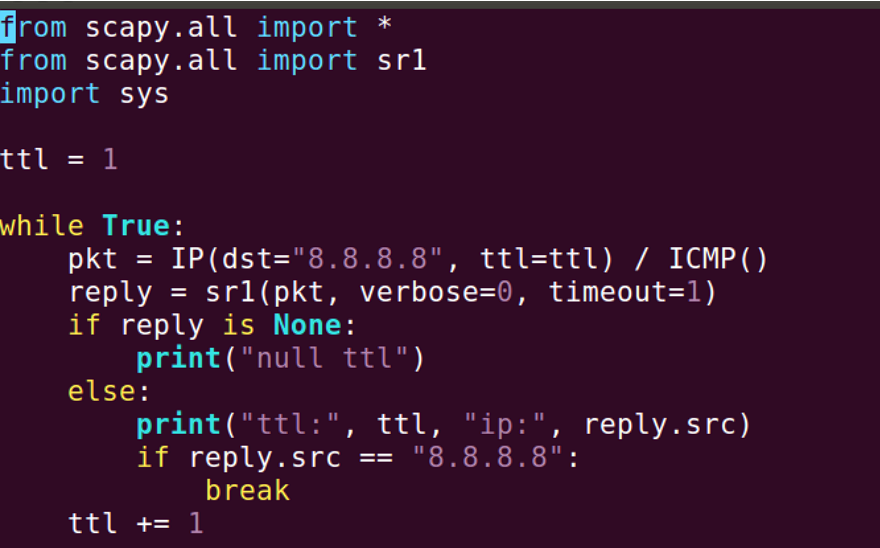
The task requires manually implementing traceroute. I wrote a Python code to implement it:
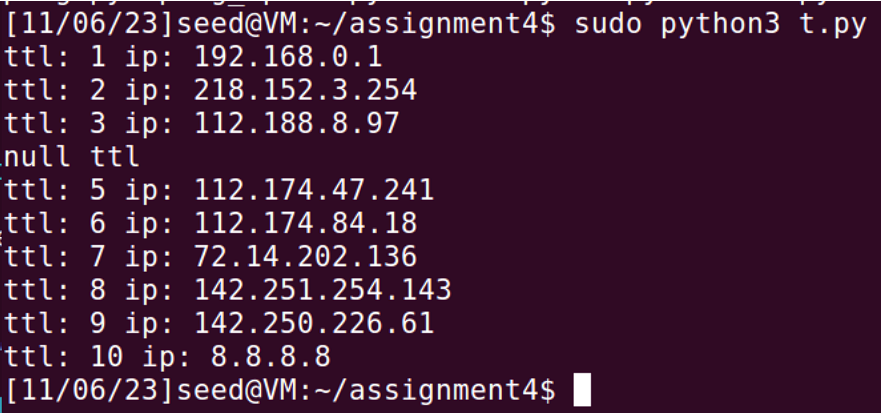
From the above observation, I can find out that it requires 10 ttl to reach 8.8.8.8
