[SEEDLAB] Cryptography Writeup (General Cryptography, ECB mode weakness, Attacking IV) #1
Task 2: Encryption using Different Ciphers and Modes.
Q1. You should try at least 3 different ciphers with ‘openssl enc’ command.
A1. Typing invalid openssl commands will give valid lists of commands.
Example commands given for encrypting/decrypting in the original material are as follows:
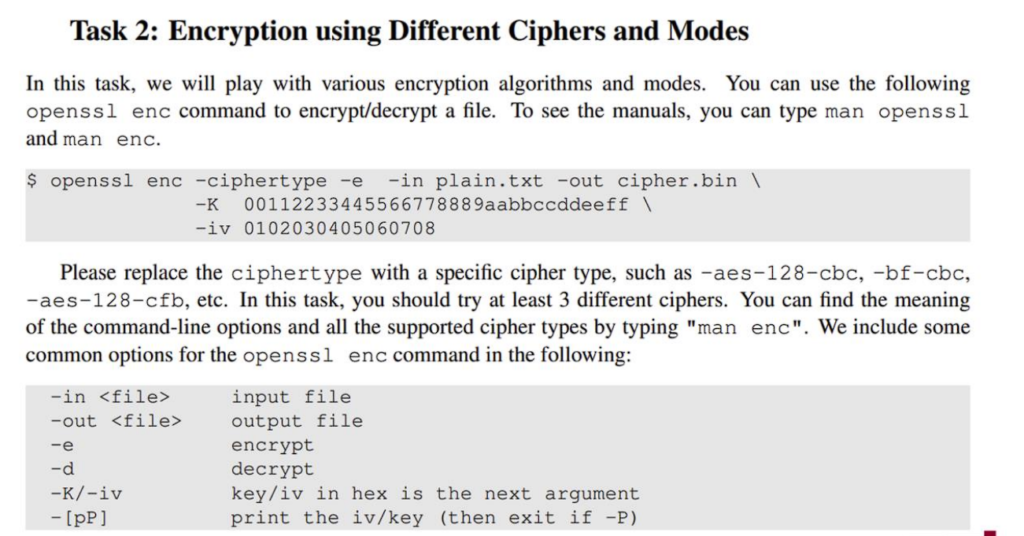
By following the commands that were given, it can solve task two as follows:
First, I made a plain.txt that contains lyrics of ‘Sunflower’ by Post Malone:
Now I am going to encrypt plain.txt with three different ciphers.
1) AES-128-CBC
KEY: e0c3439b9babbd86
IV: 2701217051801633
2) AES-128-ECB
KEY: 5e085272d4897766
3) AES-256-CBC
KEY: 5d4fa917805edae5d174e4c0dadb66cf
IV: 3189805368513145
Q2. You should successfully decrypt the cipher.bin with ‘openssl enc’ command and
describe the result in
Solution:
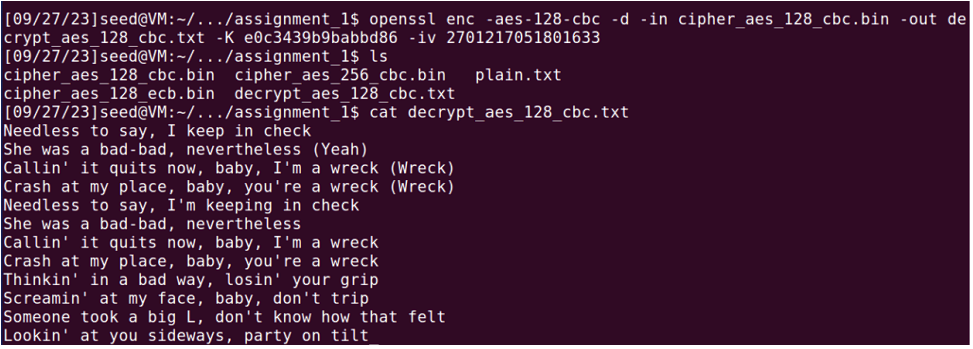
1) AES-128-CBC
KEY: e0c3439b9babbd86
IV: 2701217051801633
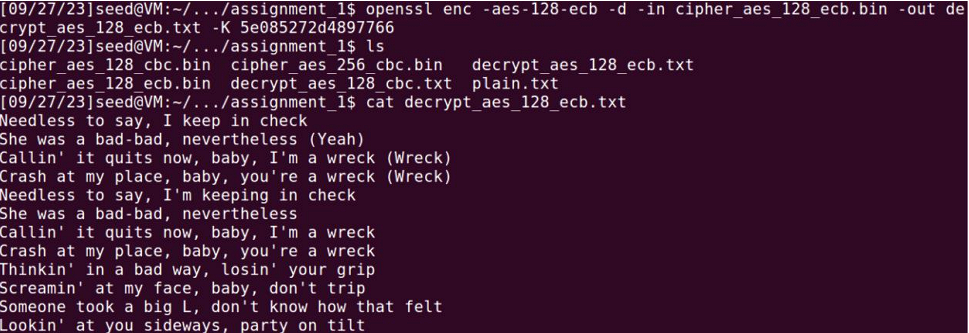
2) AES-128-ECB
KEY: 5e085272d4897766
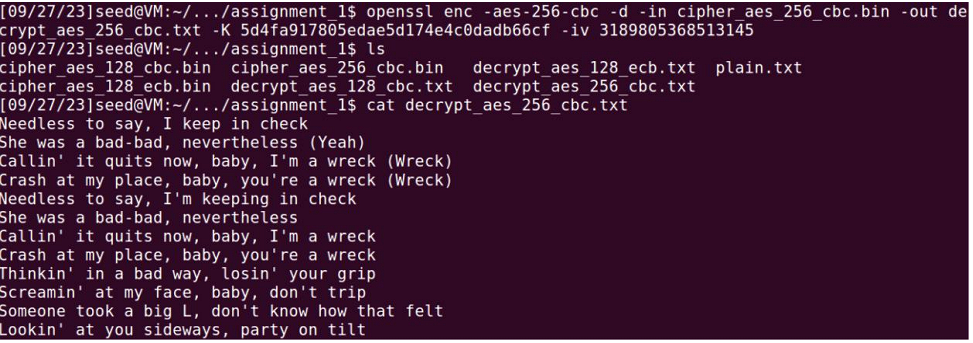
3) AES-256-CBC
KEY: 5d4fa917805edae5d174e4c0dadb66cf
IV: 3189805368513145
Task 3: Encryption mode – ECB vs CBC
- Encrypts the bmp file with AES-128-ECB.
- Encrypts the bmp file with AES-128-CBC.
- Compare the difference between ECB mode and CBC mode
I encrypted the given .bmp file with the following keys, iv, and commands:
AES-128-ECB:
KEY: 5d2afc728fd41015
AES-128-CBC:
KEY: 082b9946ed7aa3a0
IV: 0292737693132235
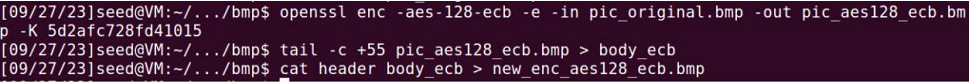
First, I got the original head of the bmp:

Encrypting with ECB Mode:
Encrypting with CBC Mode:
Q1. Please show the result of encrypted bmp image for ECB, and CBC mode to the report.
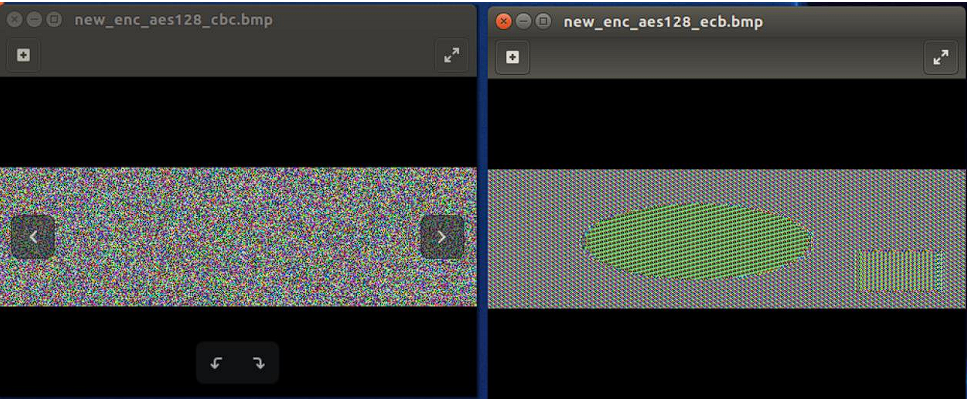
Q2. And, Can you derive any useful information about the original picture from the
encrypted picture?
A2. Yes, it gives the brief image of the original bmp picture. The original picture is as
follow:

Q3. Please explain your observations
A3. The reason is because of the characteristics of ECB mode. In ECB mode, encrypting the
same block of plaintext always gives the same block of ciphertext. And this weakness
is graphically shown in the above encrypted bmp file.
Task 4: Padding
Firstly, I picked a random binary from /home/seed/bin:
- ECB
KEY: fab76dacc8704916
- CBC
KEY: b962b31de7ab5675
IV: 3111479991242530
- CFB
KEY: 54b697b1a8748ad7
IV: 8551956343621934
- OFB
KEY: 289ee5a917ff7604
IV: 5607653827672528
Q2. Please report which modes have paddings and which ones do not
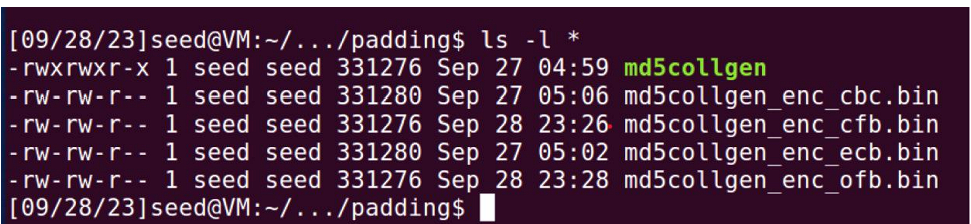
The original file size is 331276 bytes. By comparing the file size, it can determine whether the
encryption mode has padding or not.
Modes that have padding: CBC, ECB
Modes that do not have padding: CFB, OFB
Q3. For those that do not need paddings, please explain why.
CFB, OFB: Padding is not required in Counter-encryption modes such as CFB or OFB. This is
because the ciphertext is always encrypted in the same length as the plaintext. This is the reason why
it is not required.
Task 6: Initial Vector (IV) and Common Mistakes
Q1. Repeat the above experiment (①-④) with other string(P1, P2) and key, IV.
You should use -aes-128-ofb for encryption.
Q2. Show the how to find out P2 using P1, C1, and C2.
Solutions for Q1 and Q2:
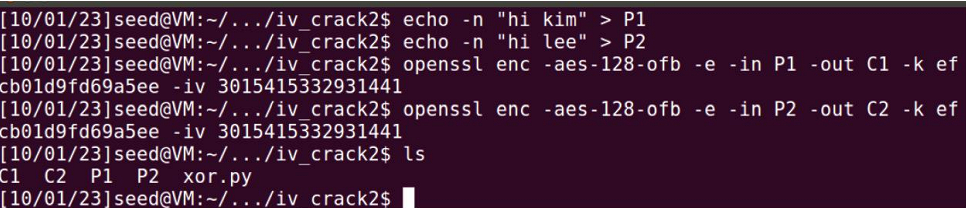
Firstly, I encrypted the following plaintext with the following key and IV:
KEY: efcb01d9fd69a5ee
IV: 3015415332931441
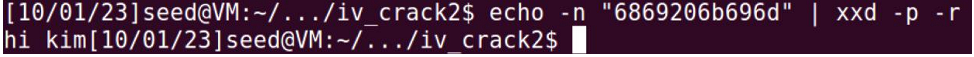
P1: hi kim
P2: hi lee
Now I tried to get P2 using P1, C1, and C2 as follow:
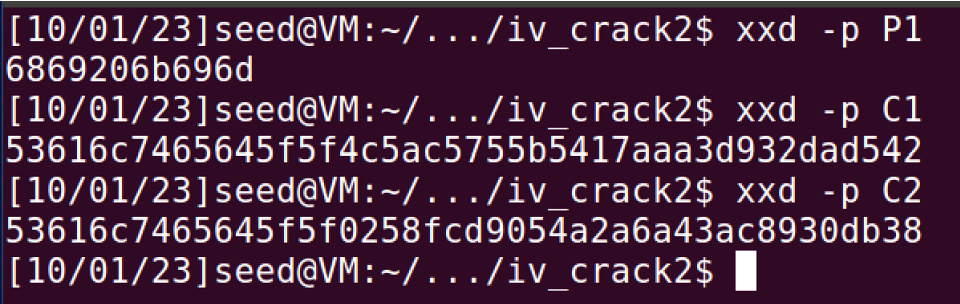
P1: 6869206b696d
C1: 53616c7465645f5f4c5ac5755b5417aaa3d932dad542
C2: 53616c7465645f5f0258fcd9054a2a6a43ac8930db38
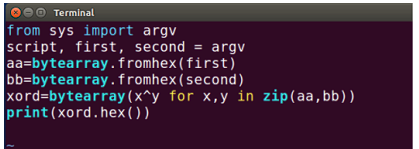
Firstly, I wrote a python program that calculates XOR:
Now P2 can be simply calculated through some XOR calculations as follows:
P1 XOR C1 == Output

Output XOR C2 == Output2
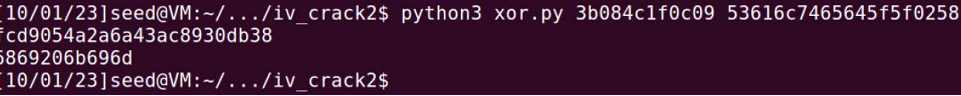
Plaintext achieved